The Beginner's Beginner Guide to DeFi
Introduction
There is no shortage of introductory content and guides to decentralized finance (DeFi). There’s one from Coinbase, Decrypt and this one from Nakamoto. These guides can be overwhelming—DeFi requires knowledge of finance , computer science, and Ethereum-development terminology. This guide assumes little to no prior knowledge and is meant to equip you with the bare necessities so that you may choose your own adventure in the world of DeFi. First is a crash course in DeFi. Second is a step-by-step guide on setting up your wallet and machine.
Crash Course — What is DeFi?
Cryptocurrencies, such as Bitcoin (BTC) and Ether (ETH) are members of a new asset class -- digital assets. BTC and ETH, in particular, are the native cryptocurrency to their own blockchains, the Bitcoin network and the Ethereum network. In addition to serving as ledgers for sending and receiving its native asset, Ethereum also possesses a virtual machine called the EVM (Ethereum Virtual Machine) with its own programming language, Solidity.
What is DeFi? It is an alternative financial infrastructure built on top of the Ethereum virtual machine. In other words, programs that run on a decentralized, censorship-resistant computer. Other blockhain networks support DeFi applications, but Ethereum by far retains the largest ecosystem and community. The Binance Smart Chain (BSC), like other centrally controlled chains, promises users DeFi-like functionality but with lower fees. These projects are known as centralized DeFi, or CeDeFi.
Smart Contracts
The fundamental building blocks of DeFi are smart contracts, which are open source programs that run on the Ethereum blockchain . They are used to create protocols in a more open, interoperable, and transparent way. Anyone can examine smart contract code and understand the outcome of their transactions—this transparency, speed, security, and rules-based behavior is what makes DeFi so appealing, specially compared to the traditional financial system. DeFi's core ethos is "code is law"—bankers or financiers cannot obfuscate how their products work, and there are no courts or legal systems to bail anyone out.
Smart contracts are frequently—but not always—designed to represent key financial concepts and abstractions. Their open-source nature then allows other programmers to quickly pull together new smart contracts by using time-tested and widely understood "financial primitives" developed by the broader community. This interoperability of components is called "composability" because primitives can easily be composed together. For more on composability and how it accelerates experimentation and innovation, refer to this essay by Brandon Iles.
DApps and DeFi
Like most software applications, DApps consist of a back-end and front-end. DApp back-ends are smart contracts running on a decentralized peer-to-peer network like Ethereum. DApp front-ends are user interfaces, hosted on regular websites, that abstract away the complexity of interacting with smart contracts directly. For individual traders and investors without a programming background, DApps are the best way to interact with smart contracts. DApps and smart contracts allow users to interact with various protocols for exchanges, lending, derivatives, asset management, and more. See the diagram below from Fabian Schär.
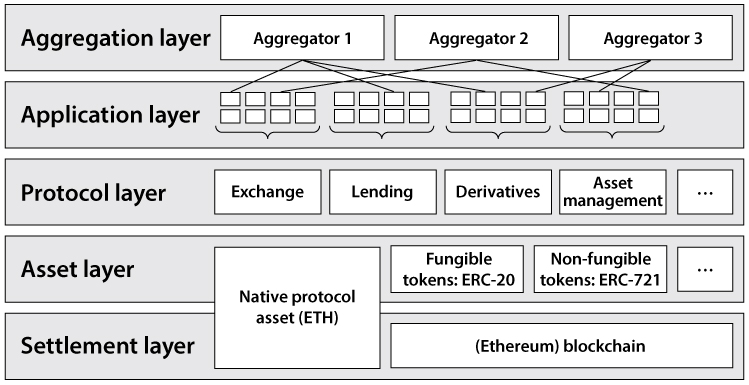
As DeFi is fast evolving, data aggregators like Coingecko or CoinMarketCap (acquired by Binance in 2020) are useful to keep abreast of weekly developments. Look at cryptocurrencies and exchanges by volume and market capitalization to get a sense of the current popular players, their tokens, and DApp usage.
Tokens
The term token may be used interchangeably with coin and cryptocurrency, however for the purposes of this guide token will be defined as “cryptocurrencies that do not have their own blockchain but live on another blockchain.”. Ethereum tokens are smart contracts, and primarily fall into two buckets: fungible and non-fungible.
Fungible tokens
Most cryptocurrencies and tokens are fungible, meaning they have sameness and divisibility: 1.0 ETH in my wallet, is indistinguishable from any other 1.0 ETH in another wallet. I can also transfer smaller amounts, such as 0.5 ETH, and combine them into larger amounts.
Prominent fungible tokens include Ample (AMPL), Tether (UST), and Dai (DAI). On Ethereum, fungible tokens follow the ERC-20 token standard, which allows these tokens to interact seamlessly with ERC-20 compatible smart contracts. Ironically, since ETH is not an ERC-20 token, ETH is "wrapped" into an ERC-20 contract called wETH so that it can be used in these contracts.
Non-fungible tokens
Non-fungible tokens (NFTs), in contrast, are indivisible and unique. Most NFTs follows the ERC-721 token standard.
One major use of NFTs is collectibles. Cryptokitties and NBA Hotshot are both NFT series created and sold by Dapper Labs in various online auction houses. One kitty or trading card cannot be subdivided, and is not in any way the same as another kitty or trading card. Many digital artists such as Beepe have tried cashing in on selling their artwork as NFTs. Memes as well have recently made their way as NFTs.
The second major use of NFTs is to represent a user's unique financial position. For example, the Ampleforth Foundation runs a rewards program for users that provide liquidity for AMPL trading. To reward users for the amount of liquidity and the amount of time it was provided, users deposit their liquidity provider tokens—which are fungible—into the Ampleforth geyser D which gives them an NFT as a deposit receipt.
Exchanges
Fungible crypto assets are bought and sold on centralized and decentralized exchanges. Centralized exchanges (CEXes), such as Coinbase and Binance, keep their system off-chain: meaning they operate as escrows for their clients, and transactions are not recorded on the blockchain. These exchanges are custodians of the traders’ funds. Given that all information, funds, and private keys in their systems, centralized exchanges are large targets for security breaches and cyber attacks.
Decentralized exchanges (DEXes), such as Uniswap, Sushiswap, and Balancer, are “peer-to-peer marketplaces directly on the blockchain”. DEXes allow traders, through the use of their cryptocurrency wallets, to remain custodian of their funds.
Lending and borrowing
Some of the other, large DeFi protocols offer borrowing in the form of margin lending. MakerDAO, Compound, and Aave are examples. A user will deposit an approved form of collateral—usually ETH—into their user account, called a "vault." A user can then borrow up to a certain percentage of the value of the collateral in a vault, usually 50%. If the value of the collateral falls below the specified threshold, then his collateral is put up for liquidation in an auction market, and the proceeds are used to pay off this debt. This is similar to how margin lending works on traditional exchanges, and carries high risks.

It's dangerous to go alone! Take this...
DeFi can be a dangerous place. It is easy to lose funds, to send to the wrong address, or to get scammed. Here we summarize some key pieces of knowledge for you to take into the crazy, dangerous world out there.
Wallets
A crypto wallet is a pair of public and private cryptographic keys. A public key allows others to make payments to the wallet, whereas a private key enables the spending of cryptocurrency. Your public key is your address. For many wallets such as Metamask or Ledger, the private key is derived from what is known as a seed phrase, typically a 12-24 word phrase.
Practically speaking, there are a variety of cryptocurrency wallets each with a drastically different user experience:
| Wallet Type | Custody | Online risk | Offline risk | Risk of loss | Description |
|---|---|---|---|---|---|
| exchange | exchange | medium | medium | medium | Keys are held by the exchange; users only need to prove their identity. Yet exchanges target of hacking, and user identities have been spoofed through SIM-swapping. |
| custodian | custodian | low | low | low | Keys are held by specialized custodian, which uses device patterns, video calls, multi-sig, and other means to authenticate ID and verify transactions. Expensive. |
| browser | user | high | medium | high | Keys stored in a web browser extension. |
| hardware | user | low | medium | low | Keys stored in small hardware device, PIN protected. |
| paper | user | low | high | medium | Keys printed onto a paper or other material, kept in secure location like in a physical vault, or under your bed. Liable to loss or theft. |
| brain | user | low | high | high | User memorizes their keys. Very high risk of loss as memory is imperfect. |
| multi-sig | users | low | low | low | N individuals can provide signatures but only M signatures are needed to execute a transaction--single lost or compromised key does not compromise the wallet. |
Wallets exist on a spectrum ranging from hot to cold. The harder it is to access assets on the wallet, the colder the wallet. Wallets that exist as desktop, mobile, or browser applications are considered hot wallets; exchange and online wallets are hot wallets. Wallets disconnected from the internet, like hardware wallets or paper wallets, are cold wallets. Hot wallets are easier and convenient to use, but easier to hack. All major exchange hacks have involved the exchange hot wallets. On the other hand, cold wallets are safer from hacks, but susceptible to theft or loss if improperly stored. More secure options do exist. But at a price. Anchorage is a custodian for investment funds, which has created more secure systems for securing digital assets—see their white paper, co-authored with BlockTower Capital.
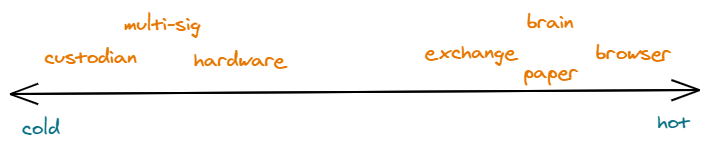
The security and/or recoverability of a wallet can be improved through multi-signature (multi-sig) protection. Multi-signature wallets have multiple possible signers, but only require a subset of signatures to approve a transaction. For example, in a 2 of 3 situation, three individuals can sign transactions, but only two signatures are needed at any one time. This arrangement can also improve recoverability. For example, two individuals can set up a 2 of 3 wallet. They sign their transactions using their respective keys, and if one of them loses a key they can use the third key as "backup".
Setting up your wallet
-
Get a wallet and set it up. Not all wallets support all cryptocurrencies and not all DeFi applications accept all possible wallets. As an ostensibly widely accepted choice, please consider a Ledger hardware wallet. The most secure approach is to buy a brand new one directly from their website (https://www.ledger.com/) and not from a distributor like Amazon, not using your real name, and have it delivered to a P.O. Box or another location that is not your home address. The names and addresses from any retailer are targets for hackers—you should not want anyone knowing you own crypto!
Here are some additional resources to help you make an informed decision:
-
Follow Ledger's device setup instructions for Ethereum, including installing Ledger Live on your computer. Make sure to enable smart contract data transactions.
-
Create an account on a centralized exchange like Coinbase or Binance.
-
Complete the additional Know Your Customer (KYC) and/or Anti-Money Laundering (AML) requirements to allow you to transfer digital assets off the exchange and to a personal wallet.
-
Buy ETH and transfer it to your Ledger — Ledger Live can help you find the "receiving" address. Double and triple check the address. Send a very small test amount first, before sending larger sums.
- Use the Ledger’s Ledger Live application to easily view your assets.
-
Download the Metamask browser extension and connect your hardware wallet. See their documentation for more information.
-
Double, triple and, quadruple check the recipient wallet address.
-
Once your Ledger is linked to your Metamask, go to any DeFi DApp and experiment with small sums to get started!
Core workflow
Once you have all of the setup done and there is ETH in your (hardware) wallet, then you are ready to really get started. The following diagram outlines the high level steps and the various boundaries of a DeFi transaction. Currently the most “popular” DApp, according to Coingecko, is Uniswap where you can swap tokens and provide liquidity. It is a good candidate as a starting DApp.
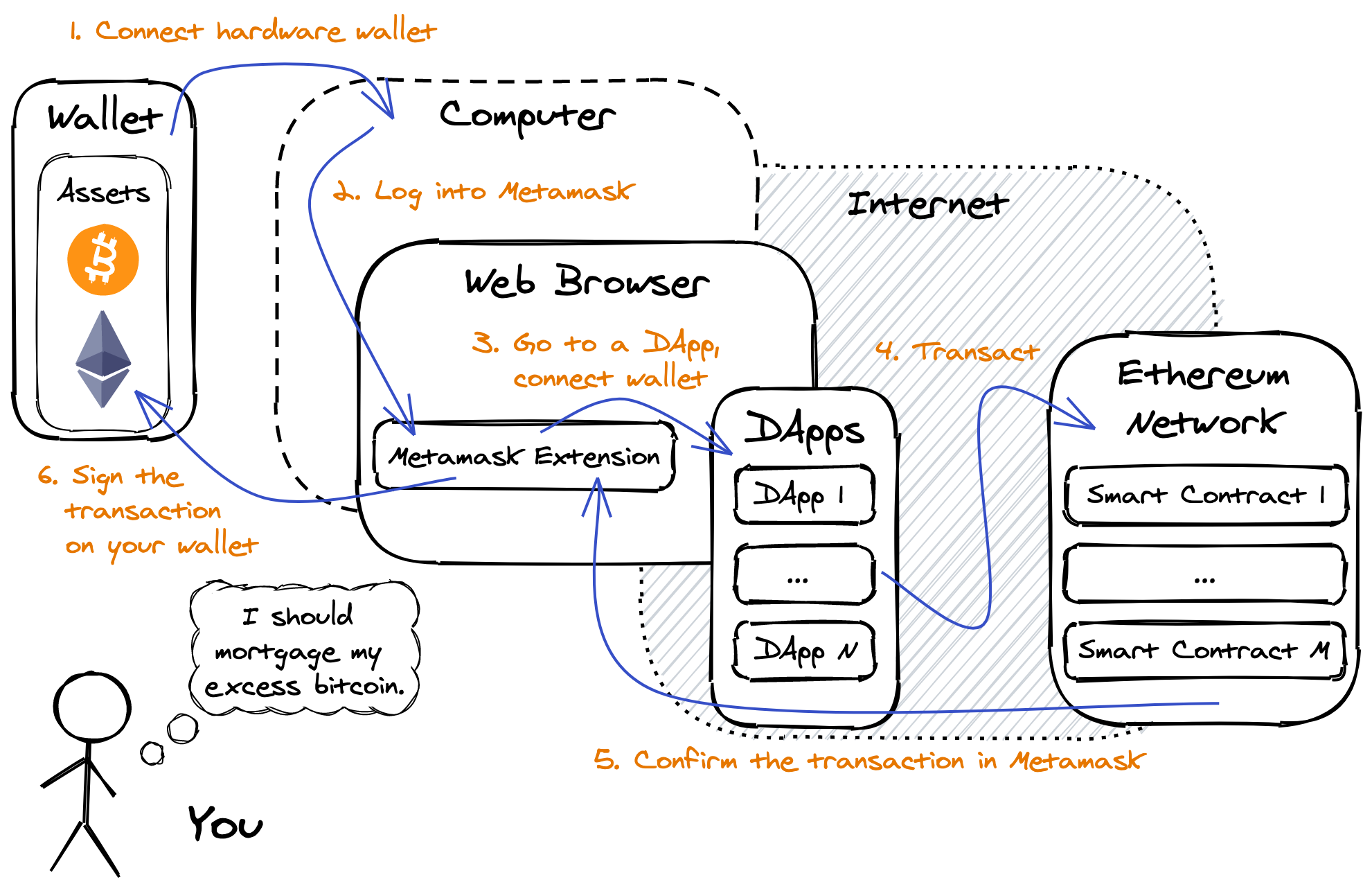
Operational Security (OPSEC)
OPSEC can be summarized as a process to protect critical information from adversaries. Establishing an intuition for OPSEC requires adopting a security mindset, a way of thinking rationally and rigorously about risk and adversaries. OPSEC encompasses the connection from hardware wallet to computer, computer to web browser, browser extension to website, etc.
From the above diagram, you can see that you need to secure the following information, ideally not all in the same place:
- Hardware wallet PIN
- Hardware wallet secret phrase
- Ledger Live password
- Computer password
- Chrome password
- Metamask password
- Metamask secret phrase
- Exchange password
- Exchange 2FA device, such as your phone or Yubikey
This guide is not comprehensive enough to cover the breadth and depth of OPSEC, however the following guidelines will help you get started and protect your assets.
Good OPSEC
- Prioritize anonymity and be socially aware; protect sensitive data online, do not tell people who you are in real life.
- Pay attention to data leaks and update your personal information.
- Use unique passwords, ideally maintained via a password manager or secured offline.
- Use encrypted software and secure internet connections and websites.
- Keep as little money in centralized exchanges as possible, and ideally no money on hot wallets.
- Use a cold wallet.
- Verify that DApps front-ends are legitimate; watch out for phishing.
- NEVER SHARE YOUR KEYS OR PASSWORDS.
Not adhering to good OPSEC is bad OPSEC; avoid doing any of the following actions:
- Publicizing your address or any other personal information.
- Talking publicly about your crypto assets, e.g. monetary value, wallet type—you don't want to become a target for thieves.
- Using text message as a form of two-factor authentication—SIM swapping is common.
- Sharing information through SMS messages—phone numbers can be spoofed can be spoofed.
- Using public or shared computers.
- Using public and/or non password protected WiFi.
- Storing sensitive information like passwords or seed phrases online, or in an unsecured computer.
There’s a lot more to be said about OPSEC and the consequences of bad OPSEC. Please check out these additional references to further calibrate your security mindset:
- https://www.schneier.com/blog/archives/2008/03/the_security_mi_1.html
- https://news.bitcoin.com/how-to-hide-your-bitcoin/
- https://blog.keys.casa/7-ways-to-level-up-your-bitcoin-opsec/
- https://news.bitcoin.com/5-opsec-errors-that-caused-cryptocurrency-users-to-lose-everything/
Technical Troubleshooting
An end-to-end DeFi transaction can be complex, and users occasionally encounter confusing and frustrating pitfalls caused by human, software, and hardware errors. One of the most publicized, costly, and unsalvageable examples of human error is the case of man that forgot the password to his wallet that contained $220 million worth of Bitcoin.
In the case of software and hardware issues, searching the support and troubleshooting documentation may help solve your problem:
- Ledger: https://support.ledger.com/hc/en-us
- Metamask: https://metamask.zendesk.com/hc/en-us
For the more technical audience, checking the GitHub issues can be very helpful as well.
Common solutions
When technical support documentation and google-ing leaves you high and dry, there are two tried and true options available. Here we summarize some solutions that worked for us.
Use latest official versions of everything:
- Browser (Chrome)
- Metamask extension
- Hardware wallet firmware
Cold rebooting
Sometimes your wallet, browser and other software are up-to-date, yet your DeFi transactions will not complete. Cold rebooting a computer is the Hail Mary pass of technical troubleshooting and it will likely solve any issues between your computer and USB devices like a hardware wallet.
You need to fully shut down your computer, not just "restart." You need to physically turn off power to your machine. This causes the BIOS and OS to be full reloaded, all starting with clean RAM. Let the machine stay shut down and disconnected from power for at least a minute. A restart is considered a warm reboot; power is not cut from the hardware, RAM is not necessarily cleared, BIOS is not necessarily reloaded.
There are complexities and exceptions to the above that vary based on the OS and other factors like computer hardware:
-
macOS / OS X:
-
For Intel based Macs the problem of USB devices not working correctly could be solved with actions like resetting the SMC, PRAM, or NVRAM
-
https://osxdaily.com/2015/08/09/mac-usb-ports-not-working-fix/
-
M1 based Macs clear the NVRAM on cold reboot.
-
-
Windows fast shutdown setting preserves old data between shut down. It is recommended to disable that setting to ensure cold reboots.
Into the wild!
A great deal of information was covered in this beginner’s beginner guide to DeFi. It hopefully provided enough fundamental knowledge and practical skills to help you simply get started. There are a plethora of concepts, ideas, and activities not covered in this guide, however, we hope we have provided you the tools to start exploring. The next steps are truly up to you. Follow your curiosity to the next chapter of your DeFi adventure.